ASIA ELECTRONICS INDUSTRYYOUR WINDOW TO SMART MANUFACTURING
Mitsubishi Electric's New Tool Improves Cybersecurity
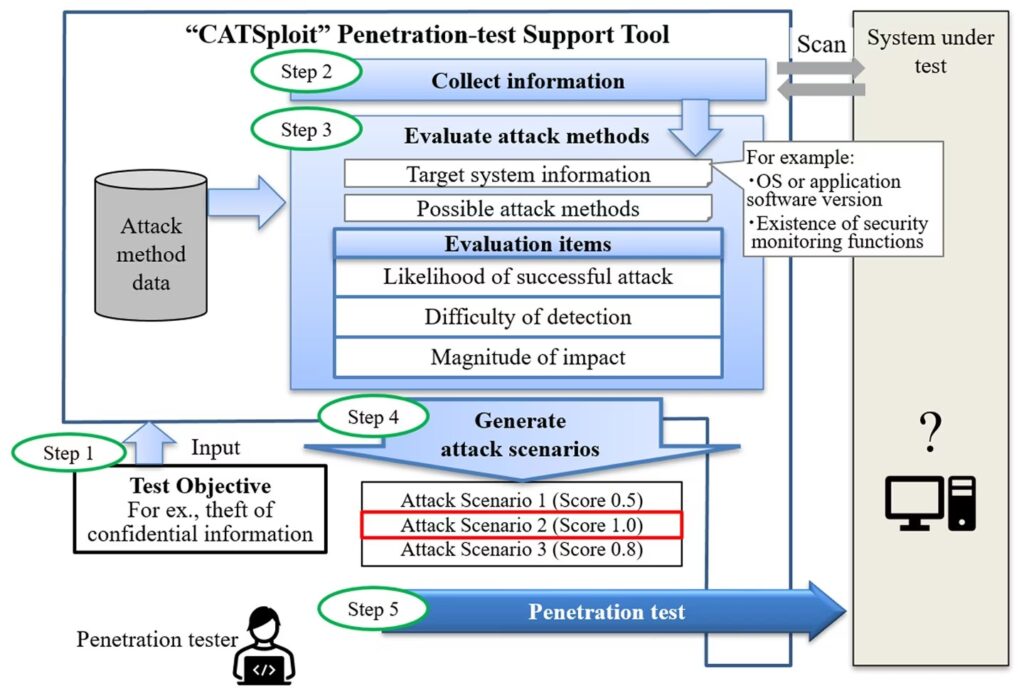
Mitsubishi Electric Corporation has developed the world’s first1 penetration-test2 support tool, CATSploit. Particularly, it automatically generates attack scenarios based on the test objectives of a penetration tester, such as the theft of confidential information. Thus, evaluating the effectiveness of test attacks. Using the attack scenarios and resulting test results (scores), even inexperienced security engineers can easily perform penetration tests.
Sophisticated Testing
In recent years, control systems including infrastructure and factory equipment, among others, have become increasingly connected to networks. Therefore, there is a higher risk of disruptions, such as power outages or public transportation shutdowns, due to cyberattacks. The need to implement security measures in such systems has become urgent.
In addition, ISA/IEC 624433 standards require that fuzzing4 and penetration security tests be performed on systems and equipment to evaluate their resistance to cyberattacks. This includes vulnerabilities due to implementation or configuration errors.
The level of sophistication of penetration testing is high. Thus, it requires the involvement of white-hat hackers5 to attack the system or product being tested. However, such individuals, who must possess very high levels of expertise, are scarce and difficult to find.
For that reason, Mitsubishi Electric, by focusing on the factors that white-hat hackers consider when selecting their attack vectors, has now developed a penetration test support tool. Particularly, it generates lists of possible attack scenarios and their effectiveness (expressed as numerical scores).
The company will divulge further details of the tool soon.
Notes:
1According to Mitsubishi Electric’s research as of December 5, 2023
2Test to confirm that if a system or equipment can be compromised by an actual attack
3Security Standards for Industrial Control Systems
4A test method for detecting software defects or vulnerabilities by entering invalid or incorrect data
5Ethical hackers who use advanced knowledge and computer technology to identify security issues, etc.